
The FreeBSD Diary |
 |
(TM) | Providing practical examples since 1998If you buy from Amazon USA, please support us by using this link. |
|
Setting up a FreeBSD IPSec Tunnel --- by John J. Rushford Jr
7 June 2001
|
|
This article was written by John J. Rushford Jr. jjr@alisa.org Last modified 5/26/01 See also this ONLamp article. |
|
Introduction
|
|
Recently I was approached by a friend that has a scanning and imaging
business focused on imaging legal documents for large law firms.
He has two offices one located in Denver Colorado and another in the
suburb of Broomfield Colorado. His goal was to establish networking
between these two offices so that Microsoft file sharing, print sharing
and network neighborhood browsing are fully functional between the
two offices at a reasonable cost. In addition, he wished to have a
web server and an email server to promote his business.
To meet his requirements, I chose high speed DSL connections to the internet with the local phone company using their business class DSL service. The business class DSL service is low cost, roughly $100.00 per month, and provides 5 leased public static IP addresses with network bandwidth of 1 Mbits up and down. For his two subnets, I chose two machines running FreeBSD 4.2-STABLE as firewall gateway machines for the two private subnets being built. In addition to the firewall functionality, the FreeBSD machines would act as his web server, mail server, and as a Samba server (see Figure 1). The gateway designated bsd1 would act as the primary domain controller for Windows, primary WINS server, and Windows master browser for the MS domain we shall call scanningcomp. In the remainder of this document, bsd1 refers to the FreeBSD 4.2 machine with the private IP address 192.168.1.254 and bsd2 refers to the FreeBSD 4.2 machine with the private IP address 192.168.2.254. These private IP's are used to configure all private subnet services. The public IP's are only only used with external DNS registration and for connecting the endpoints of the VPN. For purposes of this document, the public IP addresses are 172.16.1.254 and 172.17.1.254. Figure 1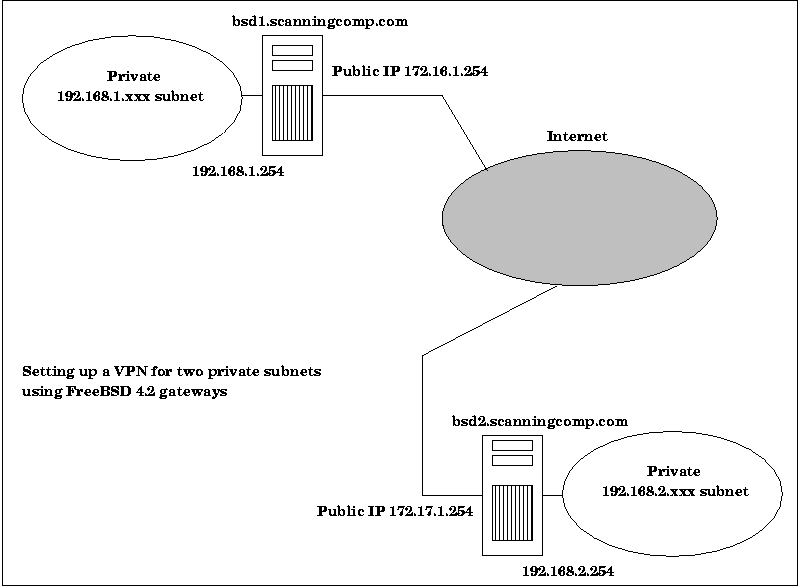
|
|
DSL Internet connection Setup
|
| The telephone company setup the DSL connections at both sites and the domain name scanningcomp.com was registered with the telephone company's primary and secondary DNS servers using the leased static IP addresses. The Cisco DSL modems were programmed in PPP mode using the instructions from the telephone company and connected to the public network interface, rl0, on both FreeBSD machines, bsd1 and bsd2. In the /etc/rc.conf file, the leased static IP addresses and netmask were configured and everything verified to insure proper operation. |
|
Microsoft networking setup
|
|
In order to facilitate Microsoft network browsing, file sharing, and
printer sharing between the two subnets, both FreeBSD machines
were loaded with Samba 2.0.7. The machines were not configured
to share any part of their disks but, only to provide network logins,
WINS services, and the synchronization of browse lists accross the
two subnets 192.168.1.0 and 192.168.2.0. bsd1 was configured as
the primary domain controller and as the WINS server for
both subnets. bsd2 was configured as the master browser
for its subnet and as a proxy WINS server with the
WINS server pointed at bsd1.
All the Windows PC's were configured to obtain their IP addresses from bsd1 or bsd2 as appropriate using the DHCP server loaded on the two FreeBSD machines. The DHCP servers were configured only to run on the private network interfaces and in addition to providing the IP address to a PC it also provides the respective default route, the domain-name, the domain-name-servers (which are bsd1 at 192.168.1.254 and bsd2 at 192.168.2.254), broadcast-address, and netbios-name-servers 192.168.1.254. bsd1 was configured to be the mail server for the domain with the appropriate DNS MX record set in the telephone companies DNS servers. Microsoft Outlook on all PC's is set to use bsd1, 192.168.1.254, as the SMTP and POP3 server. /usr/ports/mail/qpopper was loaded and configured on bsd1 Also, named was configured on both machines to provide DNS services where forwarding to the telephone companies DNS servers is used. Both bsd1 and bsd2 act as the primary DNS server for 1.168.192.in-addr.arpa and 2.168.192.in-addr.arpa as well as the domain name scanningcomp.com so that bsd1 may resolve and allow mail relaying from the PC's. The Cw flag was set in /etc/mail/sendmail.cf to scanningcomp.com and The /etc/mail/sendmail.cw file was also set to scanningcomp.com. Managing user ids and other servers is done with Webmin which is loaded only on bsd1. The user id module on Webmin is configured so that the smbpasswd is set along with the unix password so that the two passwords are synchronized. |
|
FreeBSD 4.2-STABLE kernel configuration
|
Both FreeBSD machines are configured as firewalls for their
respective subnets and are configured for IPSec required for the
IPSec tunnel. The relevant kernel configuration options
used are:
In enabling the firewall the following relevent options are set in the /etc/rc.conf file:# IP security (crypto; define w/ IPSEC) options IPSEC options IPSEC_ESP options IPSEC_DEBUG # Generic tunnel interface pseudo-device gif 4 # Berkeley packet filter used by dhcp server. pseudo-device bpf 4 # Firewall flags options IPFIREWALL options IPDIVERT options IPFILTER options IPFILTER_LOG gateway_enable="YES" defaultrouter="172.x.1.110" # assigned by the telephone company firewall_enable="YES" firewall_type="open" natd_enable="YES" natd_interface="rl0" named_enable="YES" |
|
FreeBSD 4.2-STABLE IPSec tunnel configuration
|
|
In order to provide for automatic IPSec key exchange between
the two FreeBSD machines, you must load the port
/usr/ports/security/racoon provide a configuration
file (/usr/local/etc/racoon/racoon.conf), key file
(/usr/local/etc/racoon/psk.txt), and start the
/usr/local/sbin/racoon daemon at boot time.
I found that I did not have to modify the default configuration file so, I left /usr/local/etc/racoon.conf untouched. I edited the key file, /usr/local/etc/racoon/psk.txt, and installed my private encryption keys: The key file must be protected and set to mode 0600 otherwise racoon will not run:# /usr/local/etc/racoon/psk.txt # IPv4/v6 addresses # 192.168.1.254 foobar 192.168.2.254 foobar To automatically start racoon at boot time, I created the /etc/rc.local startup script with the following:# chown root.wheel /usr/local/etc/racoon/psk.txt # chmod 0600 /usr/local/etc/racoon/psk.txt To make the IPSec tunnel connection and to add the route between the two private subnets, I wrote the following shell script and installed it at /usr/local/etc/rc.d/tunnel.sh#!/bin/sh # # /etc/rc.local # # dhcp server if [ -x /usr/local/sbin/dhcpd ]; then echo -n "dhcpd " /usr/local/sbin/dhcpd -cf /etc/dhcpd.conf rl1 fi # webmin server if [ -x /etc/webmin/start ]; then echo -n "webmin " /etc/webmin/start fi # racoon key exchange server if [ -x /usr/local/sbin/racoon ]; then echo -n "racoon " /usr/local/sbin/racoon -f /usr/local/etc/racoon/racoon.conf fi WARNING: The shell script shown here has been formatted for this web page, click here to download this script:
It is important to note that the endpoints of this tunnel are
192.168.1.254 and 192.168.2.254. No broadcast traffic may be
passed between the subnets. This was important in that when
configuring Samba, you have to use the IP address of the Samba
server and you may not use the broadcast IP address for things
like remote_announce.
|
|
In Conclusion
|
| I hope that this web page proves useful to those that read it. I believe that I have been complete and that there are no errors or omissions. If you find any errors, omissions or mistakes, please let me know so that I may update this page with corrections. |
|
References
|
|